Where you see the features,
About
Avinash Yalamanchili
Serial Entrepreneur | Ethical Hacker | Speaker | Trainer | Cyber Crime Consultant | Travel Enthusiast
Avinash Yalamanchili is an Independent Security Consultant with a wealth of experience in the field of computers and the Training Industry. Avinash has dedicated his career to the world of cybersecurity and has amassed considerable expertise in this ever-evolving field. He has not only solved complex cybersecurity problems but has also played an instrumental role in creating innovative solutions.
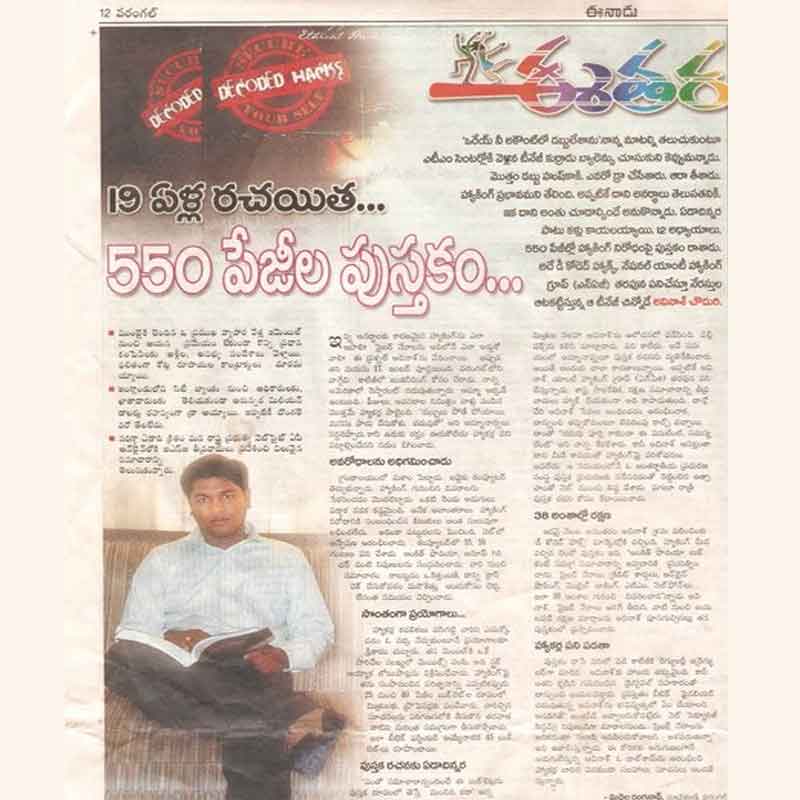
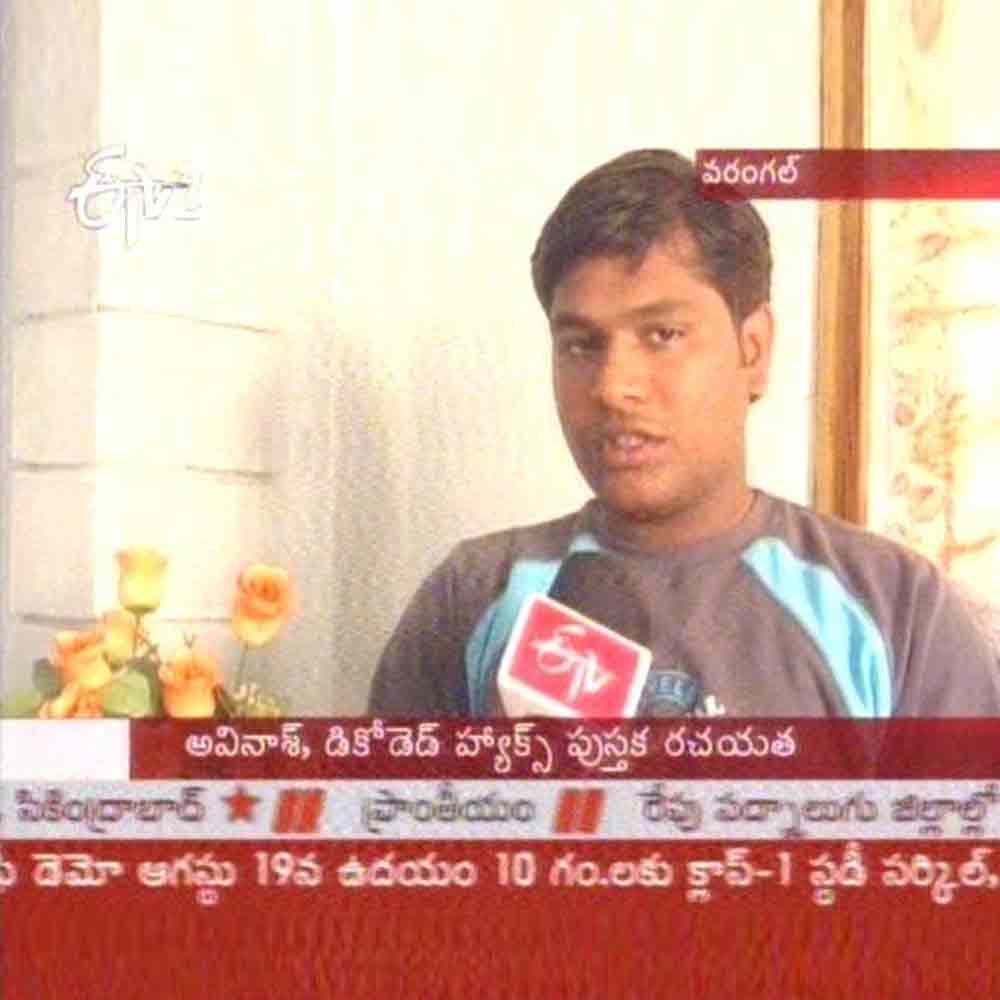
One of Avinash's notable contributions to the industry is his book titled "Decoded Hacks." This book provides valuable insights and strategies for individuals seeking to gain a deeper understanding of hacking and its ethical implications. With his extensive knowledge and expertise, Avinash has designed a distance learning course on "Ethical Hacking" to further educate and empower professionals in the digital realm.
In addition to his accomplishments as an author and educator, Avinash holds key leadership positions in the industry. He is the Founder & CEO of Siri IT Innovations Pvt Ltd, a company focused on delivering cutting-edge IT solutions. He is also the Co-Founder & CTO of Digital Ink, a platform that strives to bridge the gap between technology and creativity.
Notably, Avinash is highly regarded for his dynamic personality and unwavering dedication to his work. His ability to think outside the box and find innovative solutions has been invaluable in the realm of cybersecurity.
Milestones in Avinash's Life
Got a Computer for Rent.
Developed an interest in Computer Hacking.
His mother gifted him a PC to develop his research.
Published his first book, "Decoded Hacks," which became an instant bestseller.
Widely recognized as an Ethical Hacker, Computer Security Expert, and Founder of Anti Hackers League (AHL). Written a book, delivered seminars in various states, provided certification courses on Computer Security, Developed a secured Operating System, runs his own consulting company.
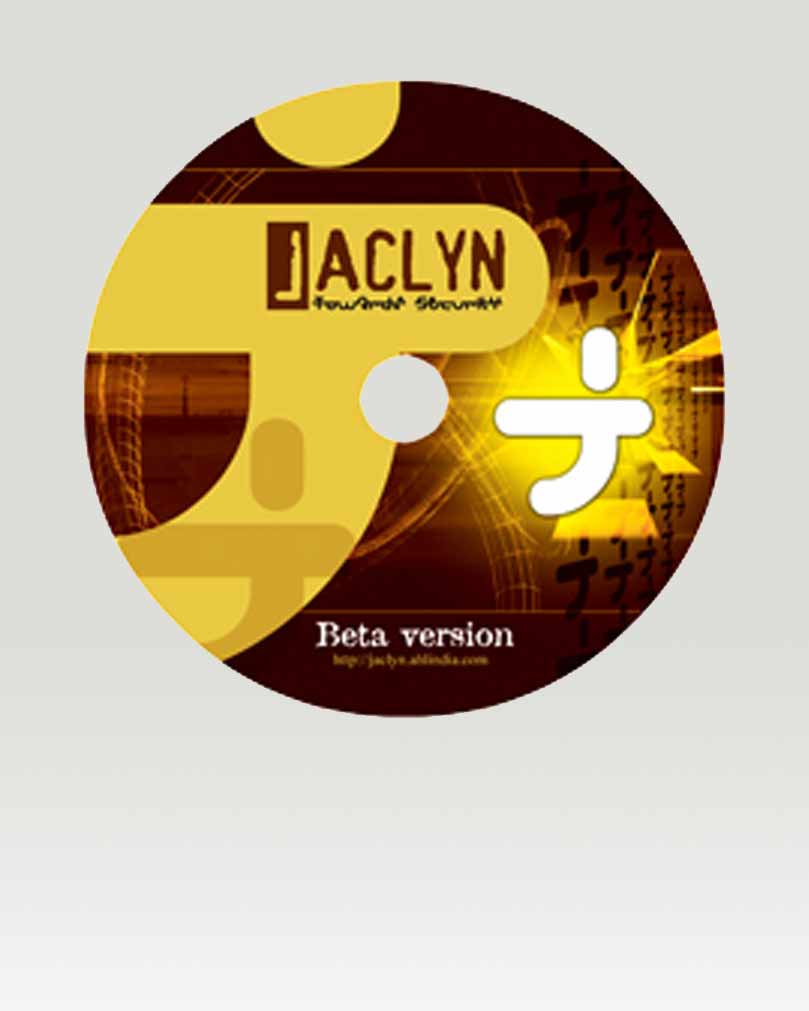
Released Hackers Operating System called "JACLYN."
Started his own consulting company, Siri Innovations, all across the Asia region.
Ventures
Book
Decoded Hacks
Every one is interested in knowing the knowledge of security norms and how to be a successful protector from Hackers. If you belong to the same community then you must have Decoded Hacks in your hands and have a glance at it. Decoded Hacks contains helpful resources that you can refer it to better protect your system from becoming the victim of Hackers.
Decoded Hacks is a handy for beginners; it is really a reader friendly book, since the existing books in market on networking are not lucid enough. A lot of source codes have been added in it for easy understanding of the topics.
It covers all aspects of emerging hacking techniques and its perfectly timed, given the current public interest in issues like web-security, cyber wars, Mobile Phone Hacking, ATM Hacking etc.People all over the world are fascinated by 'Hacking' and 'How Hackers Work?' but has no real concrete reading resource to build their knowledge base upon. Decoded Hacks has ultimate resource, which explores all aspects of Computer security, without holding back anything. Important features of the book are :
- Most comprehensive and exhaustive book on hacking
- Gives an in-depth look into Hacking techniques and source codes
- Throws light on unexplored horizons of Networking and Hacking
- Also presents even the advanced concepts in an easy to understand, newbie friendly manner.
Charity
Unleashing the power of cyber security for a safer world. Avinash Yalamanchili is on a mission to build a safer cyber world. As a passionate cyber security specialist, he tirelessly works towards community development programs, envisioning a society free from the grip of cyber crime. With an unwavering commitment to public welfare, Avinash diligently researches the latest exploits and fearlessly brings them to light. His enlightening seminars on web-security empower individuals from all walks of life, free of charge. Join him in safeguarding our digital future and let's create a world where technology thrives securely for everyone.
Empowering organizations to combat cybercrime, one seminar at a time. Avinash Yalamanchili, the force behind a safer digital world. Contact for your free seminar or workshop today. Let's make our dream of a cybercrime-free world a reality together.
If any organization is interested in having a free seminar or workshop by Avinash Yalamanchili please feel free to contact. All requests will be considered in the quest of realizing the dream… A world free of cyber crime.